
Forgot the password to your Windows admin account? There are a lot of different reasons why one would want to hack a Windows password. This tutorial will show you how to use John the Ripper to crack Windows 10, 8 and 7 password on your own PC.
SAM (Security Accounts Manager) is basically a registry file that is typically found in the latest version of Windows. The SAM file saves the user’s password into it in a hash format. The SAM file can be located at C: Windows system32 config but if you are thinking to locate this file to get access to the user’s password then it is not. Jul 26, 2012 The problem with making statements that make your bias clear, is that most often times, those statements are 100% false. The built in encryption that exists in iOS, Mac OS, and Microsoft Windows performs the exact same function as TrueCrypt and is susceptible to similar attacks ( all except iOS because of the hardware it uses ). Aug 07, 2017 Step 1: Extract Hashes from Windows. Security Account Manager (SAM) is a database file in Windows 10/8/7/XP that stores user passwords in encrypted form, which could be located in the following directory: C: Windows system32 config. The first thing we need to do is grab the password hashes from the SAM file. Decrypt Sam File Windows 7. (SAM) is a database file in Windows 10/8/7/XP that stores user passwords in encrypted form, which could be located in the following directory: C: Windows system32 config The first thing we need to do is grab the password hashes from the SAM file. Just download the freeware and unzip it on your local PC. Apr 08, 2020 Windows 7 PwDump7 This tool is developed by Tarasco and you can download it from here. This tool extracts the SAM file from the system and dumps its credentials.

Step 1: Extract Hashes from Windows
Security Account Manager (SAM) is a database file in Windows 10/8/7/XP that stores user passwords in encrypted form, which could be located in the following directory:C:Windowssystem32config
The first thing we need to do is grab the password hashes from the SAM file. Just download the freeware PwDump7 and unzip it on your local PC.
Open a Command Prompt. Navigate to the folder where you extract the PwDump7 app, and then type the following command:PwDump7.exe > d:hash.txt
Once you press Enter, PwDump7 will grab the password hashes from your current system and save it into the file d:hash.txt.
Step 2: Cracking Passwords with John the Ripper
As you can see the password hashes are still unreadable, and we need to crack them using John the Ripper. John the Ripper is one of the most popular password cracking tools available that can run on Windows, Linux and Mac OS X.
Sam File Reader
Just download the Windows binaries of John the Ripper, and unzip it.
Decrypt File Tool
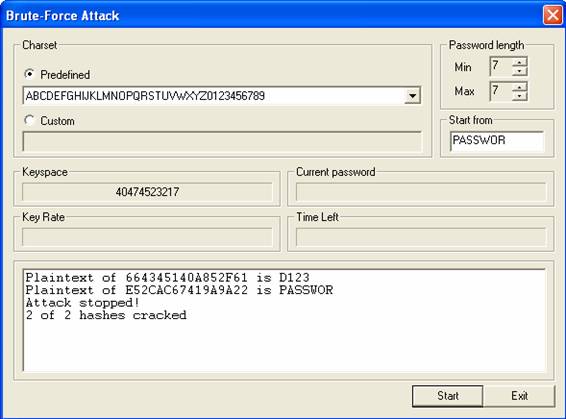
Open a Command Prompt and change into the directory where John the Ripper is located, then type:john --format=LM d:hash.txt
It will start cracking your Windows password. In my example, you can clearly see that John the Ripper has cracked the password within matter of seconds.
Final Words
Decrypt Sam File Windows 7 Download
John the Ripper is probably the world’s best known password cracking tool. But its lack of a GUI interface makes a bit more challenging to use. Don’t use it for illegal purposes.
The Windows passwords are stored and crypted in the SAM file (c:windowssystem32config). In the same folder you can find the key to decrypt it: the file SYSTEM. This two files are locked by the kernel when the operating system is up, so to backup it and decrypt you have to use some bootable linux distro, to mount the disk when the system is down or to use some program like fgdump, pwdump or meterpreter hashdump. Someone told me even that is possible to copy this files causing a Blue Sceen of Death an then remotely dump files, but I never try it.
Decrypt Sam File Windows 7 64-bit
An alternative, when the operating system is working, is to take the two twins files present in folder c:windowsrepair that the system create as a backup. This work up to Windows XP (think also Vista), but I can’t be able to find these files on Windows7. If you know something more, write me.

Sam File Location
Once you have the files you use bkhive to extract the bootkey:
Then put together the bootkey and the SAM file:
And then try to crack the hash:
This is just an exemple of use of this tools. Download driver cutting jinka 721. To crack hash you can algo use google that is always the bigest resource.